Understanding the Cyber Kill Chain: Breaking Down Each Stage to Prevent Attacks

As cyber threats continue to grow in scale and complexity, it has become essential for organisations to understand how cyber-attacks unfold. One of the most effective frameworks for this purpose is the Cyber Kill Chain, a concept originally developed by Lockheed Martin to identify and mitigate attacks by breaking them down into distinct stages. This model gives cybersecurity teams an organised approach to detect, analyse, and disrupt cyber threats at every phase. In this post, we delve into each stage of the Cyber Kill Chain, providing insights into the tools and techniques attackers use and exploring how organisations can defend against them.
What is the Cyber Kill Chain?
The Cyber Kill Chain is a seven-stage framework that outlines the stages attackers go through to breach a target system, from initial planning to execution and eventual data exfiltration. By understanding this chain, cybersecurity professionals can take proactive steps to interrupt the attack at each stage, thereby reducing the likelihood of a successful breach.
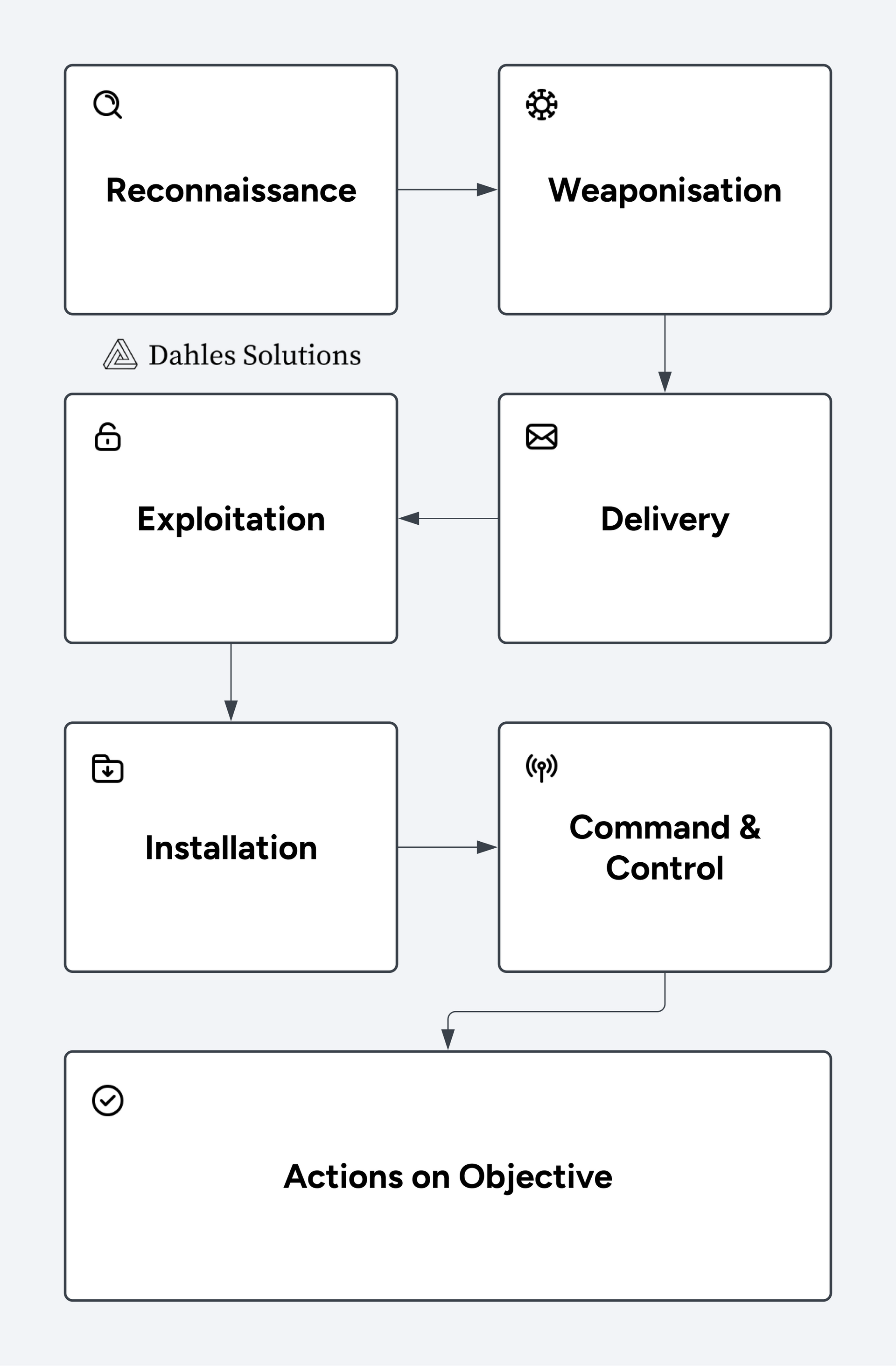
Stage 1: Reconnaissance
In the reconnaissance phase, attackers gather as much information as possible about their target to identify potential vulnerabilities. This may involve passive techniques, like reviewing publicly available data, or more active methods, like using social engineering or dumpster diving to gather confidential information. Attackers commonly scan for:
- IP addresses and network information
- Employee information on social media
- Organisational structure and recent job postings
- Publicly accessible security settings and configurations
Defensive Measures:
Organisations can mitigate risks during the reconnaissance phase by limiting the amount of public information available. Conducting regular audits of publicly accessible data, monitoring for suspicious activity, and implementing employee training to recognise social engineering attempts can all reduce exposure at this stage.
Stage 2: Weaponisation
Once attackers have gathered enough information, they move to the weaponisation phase, where they create malicious software or code designed to exploit specific vulnerabilities. This often involves pairing an exploit with a “payload”—a harmful piece of code meant to execute once the vulnerability is triggered. Common payloads include ransomware and spyware.
Defensive Measures:
Proactive defence measures at this stage include using advanced threat detection systems that identify known malicious codes and continually updating software and systems to address any newly identified vulnerabilities. Network segmentation can also help isolate systems, preventing a single point of compromise from affecting the entire network.
Stage 3: Delivery
In the delivery phase, attackers seek to transmit the malicious payload to the target system. Delivery methods vary depending on the target and include phishing emails, infected websites, or compromised USB devices. Phishing (or spearphishing) remains one of the most common delivery mechanisms, as it exploits human behaviour rather than technical flaws.
Defensive Measures:
Strong email filtering systems, employee training, and stringent endpoint security are crucial for reducing delivery success rates. Sandboxing—running attachments in a secure environment before allowing access—can also prevent malicious code from entering the organisation’s main systems. Cybersecurity awareness training is essential to help employees recognise and report phishing attempts.
Stage 4: Exploitation
During the exploitation phase, attackers take advantage of the vulnerability they identified in the reconnaissance stage to execute their malicious payload. The success of this phase depends on the target's security gaps, such as outdated software or weak access controls.
Defensive Measures:
A robust patch management strategy is crucial in this phase, as many exploits take advantage of known vulnerabilities that could be easily patched. Additionally, limiting user permissions to the minimum necessary for their roles reduces the attack surface, restricting what an attacker can do if they gain access.
Stage 5: Installation
If exploitation is successful, the attacker installs the malicious payload onto the target system, establishing a foothold within the network. This could be a backdoor or a rootkit, allowing the attacker to return to the system and expand their access.
Defensive Measures:
Endpoint Detection and Response (EDR) solutions and advanced antivirus software can help detect and block malware installation attempts. For organisations with a higher risk profile, adopting a Zero Trust model ensures that each action within the system is scrutinised, minimising the impact of any successful installation.
Stage 6: Command and Control (C2)
After installation, the attacker seeks to establish a Command and Control (C2) channel to communicate with the compromised system remotely. This allows the attacker to issue instructions, such as moving laterally across the network or exfiltrating data. C2 traffic often disguises itself as legitimate network activity to avoid detection.
Defensive Measures:
Network monitoring is crucial at this stage, as it helps detect abnormal traffic patterns indicative of C2 activity. Security teams should use Intrusion Detection Systems (IDS) and advanced behavioural analytics to identify unusual data flows. Blocking known malicious IP addresses and using network segmentation can also limit an attacker’s ability to establish a C2 channel.
Stage 7: Actions on Objectives
In this final stage, the attacker completes their objective, which may include data exfiltration, destruction of data, or disruptive attacks. At this point, the attacker has access to the data or systems they targeted and can carry out their end goal, whether financial gain, espionage, or sabotage.
Defensive Measures:
To prevent data exfiltration, organisations should employ Data Loss Prevention (DLP) solutions that monitor and restrict data transfers. Logging and monitoring data access provide visibility into potential exfiltration activities, helping security teams identify unusual access patterns and take action before significant damage occurs.
Breaking the Chain: A Layered Approach to Cyber Defence
Preventing a cyber-attack requires a layered approach that aims to disrupt the attack at multiple stages. By addressing vulnerabilities at each stage of the Cyber Kill Chain, organisations can significantly reduce their risk of falling victim to a breach. Dahles Solutions takes a holistic approach to cybersecurity, implementing robust defences across every layer. Our services include:
- Red Team Security Audits that simulate real-world attacks to test an organisation’s defences.
- Advanced Threat Detection Systems and network monitoring to identify and block suspicious activity.
- Cybersecurity Consultations to help design resilient security architectures.
- Employee Training to empower your team as the first line of defence.
Understanding and mitigating each stage of the Cyber Kill Chain is critical to protecting your organisation in today’s threat landscape. At Dahles Solutions, we combine deep technical expertise with strategic planning to help your organisation stay resilient against cyber threats. Connect with us to learn how we can strengthen your defences across every stage of the Cyber Kill Chain.
Further reading about this subject



